Ever since I wrote my Pragati piece on the two bad recent pieces of regulation by the Reserve Bank of India, and since I had a long conversation with Deepak Shenoy about them, and since (I believe) Raghuram Rajan replied to my Pragati piece in a subsequent speech, and since I got a mail from Citibank that starting next month I can’t use my internet password as a second factor authentication and must instead use a One Time Password, and since I realised I’m traveling abroad next month, and am not planning to use international roaming to be able to receive the One Time Password, I’ve been thinking of ways in which a bank or a credit card company can securely use a second factor of authentication without really inconveniencing the customer.
Essentially, a second factor of authentication is the provision of a piece of information that is not stored on the magnetic strip or pin of your credit/debit card. This ensures that the possession of your card alone will not allow a fraudster to defraud you, unless he is also in possession with the second factor of authentication. This makes is much less likely for credit card fraud to happen (but not entirely foolproof – what if the same guy steals both your credit card and your phone? – but it is impossible to design systems to that degree of security).
The four digit PIN that you have to enter when you use an ATM is one such second factor authentication (remember the note the bank sends you along with your card telling you to not write down the PIN anywhere close to the card). Similarly, the four digit PIN you have to enter to authenticate a CHIP transaction on your credit card is a second factor. Earlier credit cards would require you to sign as a second factor, but that was done post payment processing, so that is not seen as a reliable second factor – and hence they are being phased out. In the United States, for example, your ZIP code (a piece of information not available on your card) is your second factor (in the rare case it is asked for – the US is among the last major countries to move to two factor credit card transactions).
Given that it could be just about any piece of information not available on your card that can be a second factor, it is puzzling that most banks and credit card providers insist on a One Time Password sent over SMS or email as being the second factor. It is as if they believe that telecom networks are far more secure than any other way to disseminate a second factor of authentication. A friend who was visiting from the US, for example, was unable to transact online in India since his Verizon package didn’t provide him SMS services – it has gone out of fashion there.
Earlier today I was reading this excellent piece on how the US’s move towards Chip and PIN cards (will take half a decade for the transition to be complete – interestingly India made this transition in less than a year) is going to lead to higher security for credit card transactions worldwide. Among other things, the piece mentions a “Visa Token Service” where a dynamic token will replace the static credit card number.
I have had a trading account with Kotak for a few years now, and they have provided me with a physical token. Upon pressing the only key on the token, a six figure number is displayed, which is my additional factor of authentication that I need to log on to the website and transact securities. The algorithm of my token is synced with my account (basically it’s to do with the seed of the random number generator that operates on my token), and thus I get authenticated.
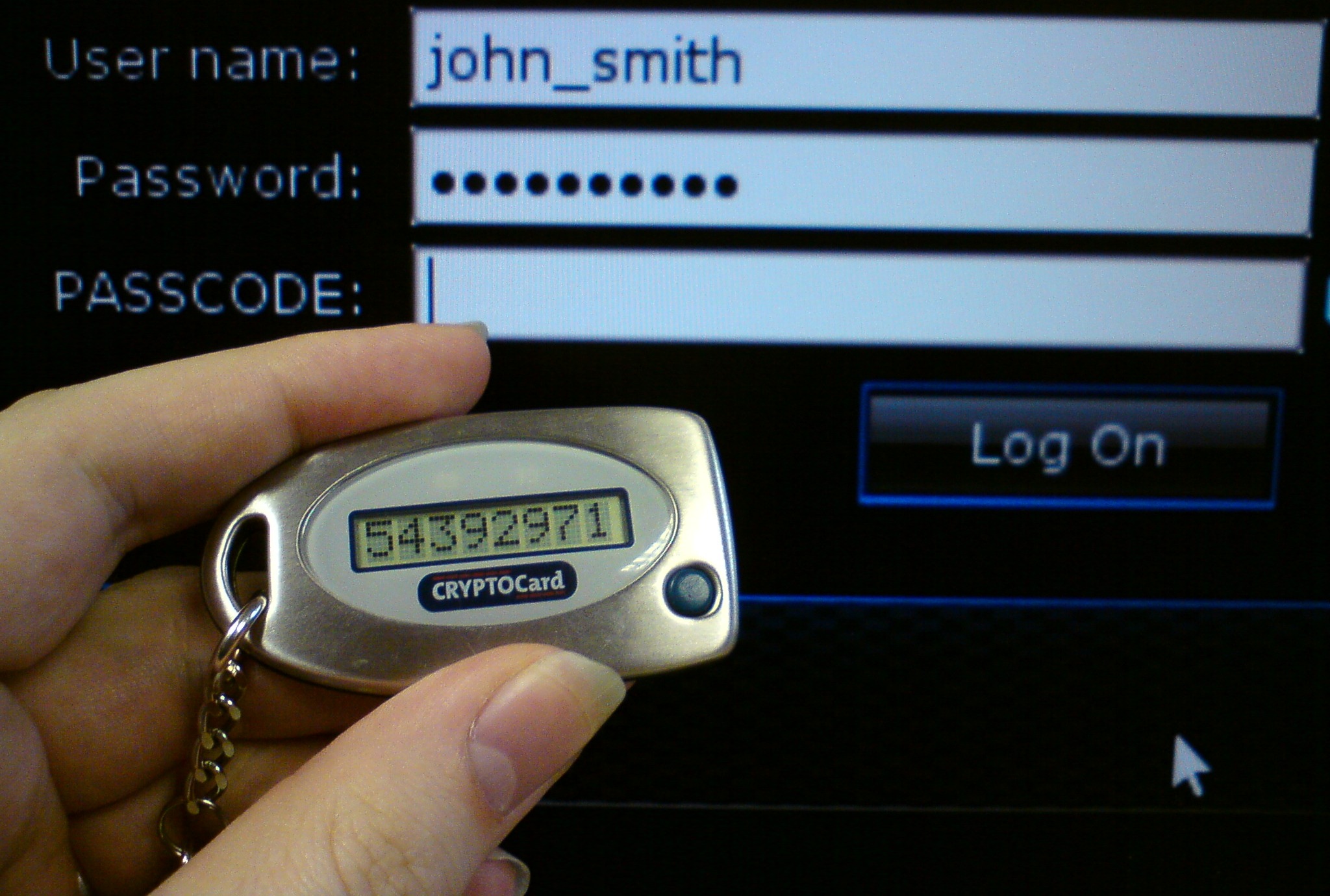
My last employer had issued us Blackberrys for work email (this was in 2009, when they were in fashion). They had also issued us tokens that we could use to log on to the corporate network from home – in the rare case when we had to login from home. And since I got the token after I’d got my blackberry, the token simply sat as an app in my blackberry. Considering that this second factor authentication is just a six digit random number set to a certain seed, why can’t my second factor of authentication be tied to one such token that resides in the Citibank app on my phone (which is already authenticated), rather than being sent to me by SMS?
This is only one possible method in which the second factor could be authorised. For transactions on taxi services, for example, your credit card details can still be stored with the taxi service, but at the end of the service on your way out you simply enter a four digit passcode into the driver’s app (the passcode could be generated by your app, or your phone and the driver’s phone can do an NFC handshake).
As I had mentioned, the opportunities for a second factor authentication are endless, but for some reason banks seem to be hell-bent on using a SMS-based One Time Password. Could it be a conspiracy by the telecom companies to maintain at least some of their SMS revenues?
And I think we need a statement from the RBI Governor stating that banks are not obliged to use a SMS-based OTP as second factor authentication, and they can be creative with it!
HSBC had the token system even in 2006, and with smartphone apps, even the hassle of carrying the token is gone. Looks like a consulting opportunity!
Seems too trivial to be a consulting opportunity! 🙂
So, my guess is the use of SMS is the mode with minimal setup time in India. The logic is “everyone now has a cell phone”.
We faced the same issue as you did on our trip to Italy, however I notice that all of our Visa cards had the “Verified by Visa” option to bypass the OTP. While this is not really a second factor (it’s another password), one could use this mode to use your card when abroad.
One alternate option is to provide a list of 2-factor options when you key in the number (sms, email, hard token etc). Good software can be then used to improve usability (have a “default” set during creation of the account). However, adding more avenues to share 2-factor token means it increases the risk of a compromise a little bit.
Finally, US banks are guilty of being really slow on adapting 2 factor auth and cards with chip. So, let’s not use them as role models 😉
Thanks! So far I was using Mastercard SecureCode to bypass OTP for my Citibank Debit Card, but now they sent a mail saying next month onwards that is not going to work and only OTP will! It’s rather bizarre, I tell you – or maybe I should blame myself for banking with an American bank 😛
Agree about the usage of multiple 2-factor options on demand. It’s sad that none of the banks have done anything on this matter!
Interestingly, most American banks do not mandate 2 factor Authentication within the US.
My guess (only a guess) is that banks in India are paranoid mostly because there is very little clarity in dealing with fraudulent transactions. In the US, at least for credit card transactions, it is very clear that the liability is on the seller, so consumers rarely get dinged for stolen or misused cards. On the other hard, dealing with a fraudulent transaction in India is a nightmare! If I am not mistaken, a copy of the FIR is required to claim your insurance (provide you have that).
Given all the tamasha, my guess in Banks just take the safer route, even though it murders usability 🙂